IT Risk & Advisory
Saudi Arabia’s digital economy is projected to reach $122.6 billion by 2024, driven by Vision 2030’s focus on AI, cloud computing, and cybersecurity. At Forvis Mazars Saudi Arabia, we empower organizations to thrive in this transformative landscape by delivering end-to-end IT risk and cybersecurity solutions tailored to local regulations like SAMA CSF, NCA ECC, and PDPL.
Key Market Insights (Saudi Arabia):
- $36.6B: ICT spending by 2024 (IDC).
- SAR 32.8M: Average cost of a data breach (IBM, 2024).
- 39%: Government entities actively use AI (SDAIA).
Core Challenges in Saudi Arabia
Organizations face critical risks in their digital transformation journey:
- Cyber Threats: Rising ransomware, phishing, and APTs targeting critical infrastructure (energy, healthcare).
- Regulatory Complexity: Compliance with SAMA CSF, NCA ECC, PDPL, and ISO 27001.
- Legacy Systems: Balancing modernization with aging IT infrastructure.
- Third-Party Risks: Vulnerabilities in vendor ecosystems.
- Incident Readiness: Limited crisis management plans for breaches or disruptions.
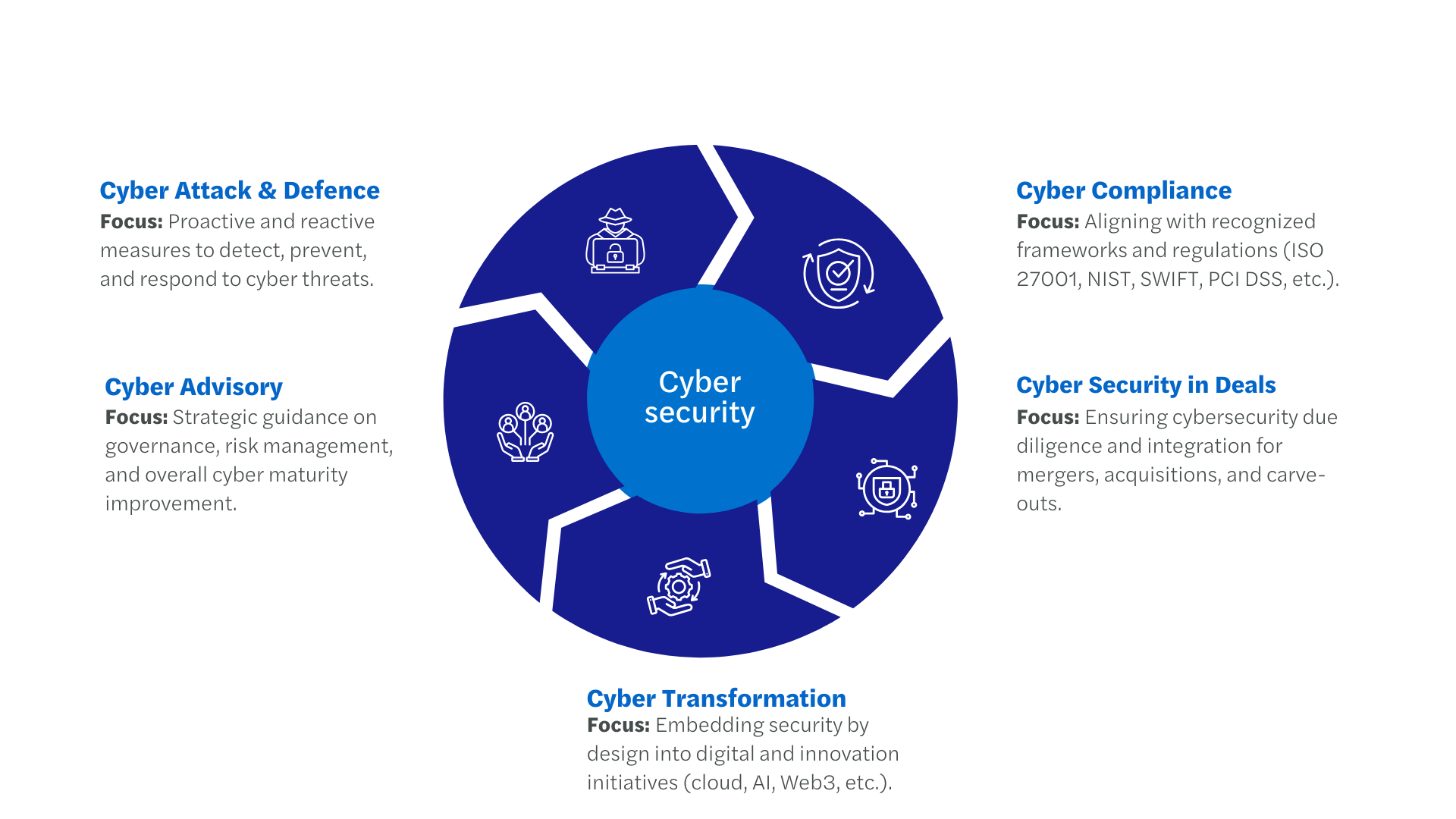
Five Core Service Pillars
Structured to address Saudi-specific challenges while aligning with global best practices.
Cyber Attack & Defence
In Saudi Arabia’s fast-evolving digital landscape, proactive and reactive threat management is critical. The Cyber Attack & Defence service safeguards organizations by simulating real-world ransomware and advanced persistent threat attacks through ethical hacking. With 24/7 SOC managed services and targeted red/purple teaming exercises aligned with NCA guidelines, this service ensures robust threat detection and rapid incident response. Additionally, digital forensics capabilities help pinpoint the root causes of breaches, enabling swift recovery and enhanced security posture.
Key Services:
- Ethical Hacking: Simulate ransomware and APT attacks to uncover vulnerabilities.
- SOC Managed Services: 24/7 threat detection using Microsoft Sentinel and AI-driven analytics.
- Red/Purple Teaming: Test defences against advanced attack scenarios (NCA-aligned).
- Digital Forensics: Investigate breaches to identify root causes.
Cyber Advisory
Effective cyber governance is essential for aligning technology with business strategy in Saudi Arabia’s competitive market. The Cyber Advisory service delivers comprehensive cyber maturity assessments against frameworks such as ISO 27001, NIST CSF, and SAMA CSF, ensuring that security measures meet both international and local standards. Leveraging CISO-as-a-Service, organizations gain on-demand leadership to steer cybersecurity strategy in line with Vision 2030, while Zero Trust-based vendor risk assessments fortify supply chains and optimize overall risk management.
Key Services:
- Cyber Maturity Assessments: Benchmark against ISO 27001, NIST CSF, and SAMA CSF.
- CISO-as-a-Service: On-demand leadership for cybersecurity strategy aligned with Vision 2030.
- Supply Chain Security: Zero Trust-based vendor risk assessments.
Cyber Transformation
Secure digital innovation is a cornerstone of modern business. The Cyber Transformation service offers rigorous cloud security architecture reviews and ISO 27017 audits to protect cloud deployments on platforms like Azure and AWS. IAM solutions—featuring role-based access control (RBAC) and privileged access management (PAM)—ensure that access to critical assets remains secure. Moreover, specialized expertise in AI/Web3 security protects emerging technologies, including smart contracts and AI/ML pipelines, empowering organizations to innovate with confidence.
Key Services:
- Cloud Security: Architecture reviews and ISO 27017 audits for Azure/AWS environments.
- IAM Solutions: Role-based access control (RBAC) and Privileged Access Management (PAM).
- AI/Web3 Security: Secure smart contracts and AI/ML pipelines
Cyber Compliance
Navigating Saudi Arabia’s regulatory landscape demands a precise and thorough approach. The Cyber Compliance service conducts comprehensive gap analyses to align practices with SAMA CSF, PDPL, and DORA requirements. It prepares organizations for stringent audit processes with SOC 2/SOC 3 reporting—particularly benefiting sectors such as finance and healthcare. Combined with resilient business continuity strategies based on ISO 22301, this service ensures organizations remain compliant, secure, and ready to address operational challenges.
Key Services:
- Gap Analyses: Align with SAMA CSF, PDPL, and DORA requirements.
- SOC 2/SOC 3 Reporting: Audit readiness for financial and healthcare sectors.
- Resilience Planning: Business continuity strategies (ISO 22301).
Cybersecurity in Deals
In high-stakes mergers, acquisitions, and divestitures, robust cybersecurity is paramount. The Cybersecurity in Deals service supports every phase of the transaction lifecycle, beginning with detailed pre-deal due diligence to assess cybersecurity readiness according to SWIFT CSP and ISO 27001 standards. During post-merger integration, identity and access management is streamlined across combined entities, while carve-out security measures ensure clean data segregation in transitional service agreements. This comprehensive approach minimizes risks and secures value throughout strategic transactions.
Key Services:
- Pre-Deal Due Diligence: Assess targets’ compliance with SWIFT CSP and ISO 27001.
- Post-Merger Integration: Harmonize IAM systems across merged entities.
- Carve-Out Security: Clean data segregation for transitional service agreements (TSAs).
Frameworks Aligned with Saudi Regulations
Our solutions ensure compliance with national and international standards while addressing industry-specific needs. By aligning with these frameworks, we help organizations build trust, enhance resilience, and achieve operational efficiency.
Key Cybersecurity Frameworks We Support
|
|
Request a Consultation
Let’s Build Your Cybersecurity Strategy Together
Whether you’re preparing for regulatory audits, responding to emerging threats, or planning a digital transformation, our team is ready to guide you. Schedule a consultation to discuss tailored solutions aligned with Saudi Arabia’s regulatory landscape, including SAMA CSF, NCA ECC, and PDPL compliance.
Contact Us