Cyber security in 2026: navigating innovation, regulation and resilience
Cyber security in 2026
Global state of cyber security
Heading into 2026, cybersecurity has become a core pillar of digital transformation. The accelerated adoption of AI represents the most profound shift since the move to cloud, introducing disruption not only through changing business strategies but also through a fast-evolving regulatory environment.
Key insights
- Leading organisations are moving beyond cyber security as a cost centre and finding strategic ways to leverage it as a competitive advantage
- Whilst AI introduces many new risks, it also offers specific opportunities that resilient organisations must consider
- With hundreds of disparate compliance and reporting requirements bogging down cyber teams, one approach is allowing businesses to grow, expand and innovate confidently
- Data governance has become the cornerstone of effective cyber security strategies; our experts share crucial advice for approaching governance strategies amidst complex ecosystems
- The cyber security skills gap continues to widen, particularly for professionals who understand both traditional security and emerging technologies
To move forward, organisations must embed cyber security into their innovation and implementation strategies whilst staying agile to adapt to evolving threats. Those that do will protect their assets and gain a competitive edge in the digital economy.
Regulatory evolution and market dynamics
In the European Union, regulations like DORA (Digital Operational Resilience Act) are moving into their enforcement phases, whilst NIS2 regulations are being translated into national frameworks across member states, with implementation deadlines extending into summer 2026. This patchwork implementation and rapid evolution creates both opportunities and challenges for multinational organisations.
Contrastingly, in the United States, the federal approach has focused more on follow-through than new regulation creation. The Cybersecurity Maturity Model Certification (CMMC) requirements for Department of Defense contractors have been enacted, whilst initiatives like the Critical Infrastructure Resilience (CIR) framework continue to evolve. At the state level, the landscape remains fragmented, with 220 different cyber and privacy measures across 38 states and 47 separate AI-related bills across 23 states.
How a risk-based approach ensures continuity without undue cost
This regulatory complexity has created what many industry professionals describe as both a burden and an opportunity. Whilst many new regulations do aim to help improve resilience and business continuity, the burden compliance creates can also be a huge weight for already constrained teams.
As the web of compliance requirements grows, organisations who take a tick-box approach will struggle to juggle disparate requirements and complex areas of overlap. In order to remain cost effective in their compliance efforts, businesses should prioritise risk-based assessments. Last year’s report details how to approach risk-based cyber security and it remains a vital strategy for cyber security teams to prioritise and address risks in a way that facilitates compliance, rather than trying to make compliance facilitate security.
_______________
Supply chain integration and the competitive advantage of cyber security
With the tech surface and supply chain of each organisation growing more complex, organisations with strong cyber postures are increasingly benefiting from reputational advantages and supply chain preferences. This trend is particularly pronounced in B2B markets, where request for proposals (RFPs) and tenders now routinely include substantial cyber security requirements, eliminating potential vendors from consideration whose cyber measures do not meet the prescribed standard.
The complexity of modern supply chains often leaves organisations unsure where their data resides or how it is processed, creating vulnerabilities, especially as AI introduces new forms of data sharing, while digitalising legacy systems expands attack surfaces and dependencies. Each organisation is now accountable for cyber security across its ecosystem, as reflected in DORA and NIS2. This shared responsibility is driving adoption of sophisticated Third party Risk Management (TPRM) frameworks, with monitoring tools that score organisations on cyber metrics creating new market pressure. Companies are discovering that their cyber maturity directly determines their ability to win contracts, secure partnerships and maintain customer trust.
_______________
Artificial intelligence: the double-edged revolution
Artificial intelligence represents both significant opportunity and unprecedented risk in the current cyber security landscape. Most organisations are rapidly adopting AI tools for efficiency gains, but many are doing so without adequate governance frameworks or understanding of the associated risks.
AI threats and opportunities in cyber security
On the defensive side, AI is transforming cyber security capabilities in several key areas:
- Network monitoring and anomaly detection
- Incident response and automation
- Code security
However, the more offensive applications of AI present significant challenges, even for AI-enabled cyber teams.
AI is giving attackers the ability to automate and personalise threats at scale. From instantly spotting vulnerabilities to generating convincing phishing campaigns, the risks are especially acute for non-technical teams.
The shadow AI challenge
Perhaps the most significant immediate risk comes from "Shadow AI", AI usage that occurs without organisational oversight or governance. The concept of “Shadow IT” is not new to cyber security teams, but the pervasive usage of AI exacerbates the threat of these unauthorised technologies. Employees are making thousands of small decisions daily with AI assistance, often inputting sensitive data into systems without understanding the implications.
AI challenges & practical implementation strategies
Agentic AI, systems designed to act without human intervention, is reshaping cyber security. Whilst promising major efficiency gains, these tools introduce risks that many organisations are only beginning to grasp.
The key challenges with agentic AI lie in ensuring proper input validation and maintaining meaningful human oversight.
Although evolving rapidly, AI regulation remains fragmented and nascent. The US promotes innovation with minimal oversight, even mandating AI use in cyber security, whilst the EU’s AI Act contrastingly offers broader, more limiting regulation, though its impact on cyber security is still evolving. This regulatory uncertainty creates challenges for organisations seeking to implement AI responsibly, especially as the market races forward with AI at the centre.
To stay resilient, organisations must not delay innovation but instead must adopt governance frameworks that evolve alongside regulation.
_______________
Quantum computing: preparing for the paradigm shift
Whilst quantum computing may not pose an immediate threat to most organisations, the potential impact is so significant that preparation must begin now.
Understanding the quantum threat
The quantum threat operates on a different timeline than traditional cyber risks. While quantum computers capable of breaking current encryption may be years away, adversaries are already employing “steal now, decrypt later” tactics. Organisations should begin transitioning to quantum safe encryption algorithms before the threat becomes acute, and the National Institute of Standards and Technology (NIST) is already releasing tools and guidance to support this shift. Though it may seem distant, organisations can and should begin quantum preparation now with the following steps:
● Cryptographic inventory: map all systems and data that rely on cryptographic protection to understand potential vulnerabilities.
● Asset prioritisation: identify which data and systems would be most severely impacted by a loss of cryptographic protection.
● Transition planning: develop migration strategies for moving to quantum-safe algorithms as they become available.
● Supply chain assessment: ensure that vendors and partners are also preparing for the quantum transition.
_______________
Data strategy, transformation and governance
The “garbage in, garbage out” principle needs addressing more urgently than ever, as AI-driven decisions rely on high-quality data which consequently makes governance central to cyber security. Poor data governance creates cascading risks that extend far beyond traditional data protection concerns. During incidents, organisations often discover previously unknown data stored in unmonitored locations with unclear access controls.
This lack of visibility not only creates unknown attack surfaces, data that is not properly catalogued cannot be adequately protected, but it can also create compliance risk.
Third-party risk management and data sharing
As data sharing grows more complex, third-party risk management (TPRM) has become an essential cyber concern. Multi-layered supply chains often obscure how data is processed and protected, increasing exposure. Effective TPRM requires several key components:
● Service level agreements (SLAs) with security controls: contracts should explicitly define security and compliance requirements, with the right to audit included wherever possible rather than relying on self-reporting.
● Regular assessment and monitoring: TPRM programmes are only effective if they include ongoing monitoring and regular reassessment of vendor risks, the right to audit is only valuable if it is leveraged.
● Tiered vendor management: not all vendors pose the same risk. Organisations should implement tiered approaches that focus intensive oversight on the most critical relationships.
Practical data security and governance implementation
Organisations looking to improve data governance should begin with practical exercises rather than abstract policy development. Business continuity discussions can start simply, leaders, technical and nontechnical alike, asking questions such as, “what happens if your phone and computer do not work?” and evolve into more sophisticated dialogues about data dependencies and protection requirements. This conversational approach should extend to official policies as well: cyber teams must ensure policies are simple enough for nontechnical users to follow, while education and partnership both enable the workforce to uphold them and equip governance teams with the business knowledge needed to design effective measures.
Balancing data security with business enablement remains a core governance challenge. Overly strict policies often drive risky workarounds and Shadow IT, whereas the most effective approach combines technical controls with cultural initiatives. Close partnership with business units fosters mutual understanding and compensating controls such as monitoring keep cyber teams informed of user behaviour.
_______________
Cyber teams and expertise
The cyber security workforce faces unprecedented challenges as the field evolves rapidly and the skills gap widens. Organisations need professionals who understand both traditional security principles and emerging technologies, but such expertise is increasingly rare and costly. The Chief Information Security Officer (CISO) role has evolved significantly, with CISOs now expected to act as business leaders rather than technical specialists, taking on regulatory compliance, board reporting and strategic planning.
This shift reflects cyber security’s transition from a technical function to a business enabler. Compensation for CISOs has risen accordingly, but the shortage of candidates with both technical expertise and business acumen remains a major challenge. Many organisations are turning to virtual CISOs to fill gaps and provide broader experience.
The innovation challenge
One of the most significant workforce challenges is finding professionals who can both innovate and manage, especially in medium sized organisations. The rapid pace of change demands that cyber security experts continually learn new technologies while maintaining core security knowledge. This challenge is most acute in areas like AI and quantum computing, where the intersection of advanced technology and security creates complex requirements few fully understand. To bridge this gap, many organisations are turning to trusted advisors and consultants to guide strategy and implementation alongside internal teams.
Building sustainable cyber teams
The traditional approach of hiring individual cyber security experts is becoming unsustainable as competition drives compensation beyond many organisations’ reach, while the rapid pace of change makes it difficult for internal teams to stay current. Automation and AI are helping cyber teams scale, but shared service models are increasingly common - particularly in mergers and acquisitions, where parent companies or investment firms provide capabilities for portfolio companies. External partnerships also add value, offering best practice implementations and filling expertise gaps more economically than hiring.
_______________
Quantifying cyber security value
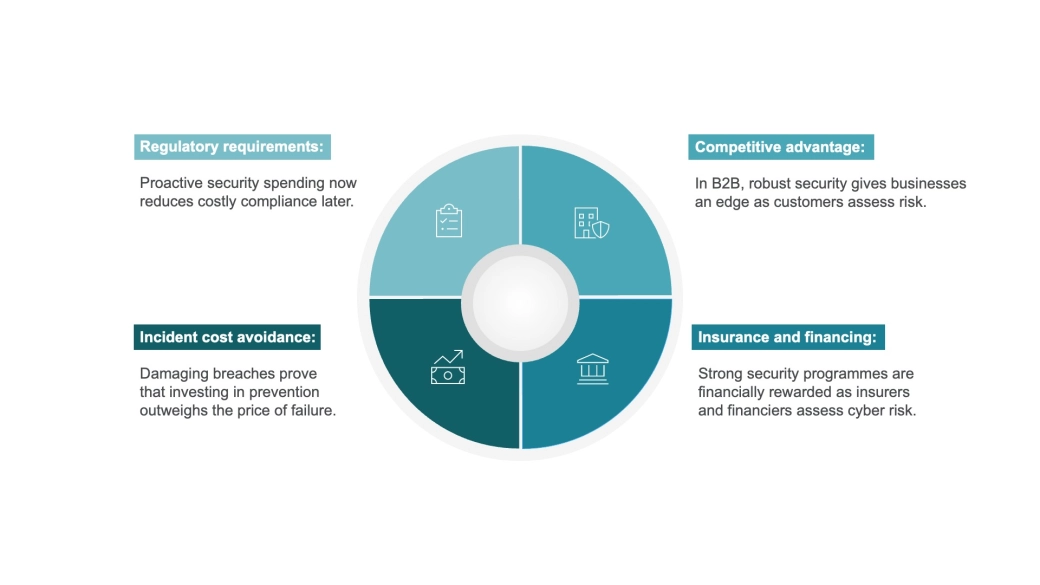
Organisations are moving beyond mere technical metrics to assess cyber security effectiveness through business impact, looking at achievements like disruptions avoided and revenue enabled by strong security. This shift is key to securing funding and demonstrating ROI.
The cost concern: cyber security as investment, not expense
The proliferation of threats and the complexity of modern technology environments can make cyber security feel like an ever expanding cost centre, but leading organisations are reframing it as strategic investment. Many now recognise the competitive advantage of strong cyber practices, which have become a key differentiator in B2B markets where customers evaluate vendor security as part of their own risk management. Compliance pressures and high profile incidents are driving this focus and cyber teams that can quantify and communicate the value of resilience unlock far greater buy in.
Beyond customers, insurers and financing institutions are also factoring cyber readiness into their assessments, offering clear financial incentives for strong security programmes.
Measuring what matters
The most successful organisations are moving beyond traditional security metrics to focus on measuring success in ways that directly relate to business outcomes and stakeholder value. This includes:
Optimising the ROI of cyber security spend
Organisations that invest in proactive cyber security measures consistently demonstrate better outcomes than those that take reactive approaches. However, with resources limited in even the largest organisations, the following investment focuses can help optimise for ROI and minimise risk:
● Risk-based prioritisation: focus both human resource and capital on protecting the most critical assets rather than attempting to secure everything equally.
● Security by Design: build security requirements into systems and processes from the beginning, rather than trying to add them later.
● Integrated approaches: look for security solutions that address multiple requirements simultaneously, reducing the need for point solutions.
● Automation and efficiency: invest in tools and processes that amplify human capabilities rather than simply adding more personnel, especially regarding continuous monitoring for ongoing visibility.
● Employee education: implement regular training and awareness programmes that reduce the likelihood of human error-related incidents and social engineering vulnerability.
● Incident response preparation: develop and regularly test incident response capabilities in full before they are needed.
● Shared services: consider shared cyber security services where appropriate, particularly for specialised expertise that does not require full-time internal resources.
_______________
What resilience looks like in 2026 and beyond
Looking ahead to 2026 and beyond, true cyber resilience will extend beyond traditional security measures. Security by Design will shift from best practice to business necessity, with organisations expected to show regulators, customers and insurers that security has been integral from the start rather than added later. This will be especially critical for emerging technologies like AI, where design choices may reveal security implications only once systems are in production. Organisations that neglect these principles risk disadvantages in effectiveness, market reception and compliance.
The pace of change will also demand governance frameworks that adapt quickly while maintaining core principles. Resilient organisations will build structures that work across boundaries, learn continuously and anticipate new threats.
As the landscape accelerates, the most resilient will focus on technology agnostic capabilities including adopting risk based approaches, creating vendor neutral architectures and developing workforce skills that transcend specific tools.
Ecosystem-wide risk management
Resilience in 2026 will require businesses to think beyond their own boundaries to consider the security of their entire business ecosystem. This includes not only traditional supply chain partners but also technology vendors, service providers and even competitors in shared infrastructure arrangements.
_______________
Cyber security must enable innovation, not hinder it
The cyber security landscape in 2026 will present both unprecedented challenges and remarkable opportunities. Organisations that approach these challenges strategically, that is to say by embracing emerging technologies whilst maintaining strong governance, investing in people and capabilities whilst leveraging automation and viewing security as a business enabler rather than a constraint, will find themselves with significant competitive advantages.
The path forward requires several key commitments:
● Embrace change whilst maintaining principles: technology will continue to evolve rapidly, but fundamental security principles remain constant. Organisations must be agile enough to adapt to new technologies and at the same time stay consistent enough to maintain strong security postures.
● Invest in people and partnerships: the cyber security challenges of 2026 and beyond will require capabilities that no single current organisation can fully develop internally. Strategic partnerships and continuous workforce development will be essential.
● Measure business impact: security programmes must demonstrate their value in business terms, not just technical metrics. This requires cyber security professionals to develop business acumen alongside technical expertise.
● Think ecosystem-wide: individual organisations cannot achieve true resilience in isolation. Cyber security must be approached as a shared challenge requiring coordinated responses.
Organisations that thrive will view cyber security not as a constraint but as a key enabler of innovation. By embedding security into their DNA, they can seize emerging technologies while maintaining stakeholder trust. Looking to 2026 and beyond, success will depend on preparing today, building the capabilities, partnerships and governance needed to navigate a complex, evolving threat landscape and capitalise on new opportunities.